Security isn’t just about building walls; it’s about building trust.
That’s why we’ve taken a leap towards transparency by making Otterize open source.
We believe in security for all
Transparency, innovation, and trust are at the core of our mission. Join us in shaping a safer digital future, together. Explore, contribute, and strengthen security with Otterize.
Transparency builds trust
See the code, trust the code. Our open source approach ensures transparency and accountability.
Constant evolution
Security never stands still. By going open source, Otterize stays on the cutting edge of protection. Join us in shaping the future of security.
Community-powered innovation
Collaboration fuels innovation. With open source, we invite you to join our community and share ideas, and build a secure digital world together.
What are you waiting for? Experience the power of Otterize OSS for yourself
Simplify network policy management
Why make things complicated when they can be simple? At Otterize, we’re all about making your life easier.
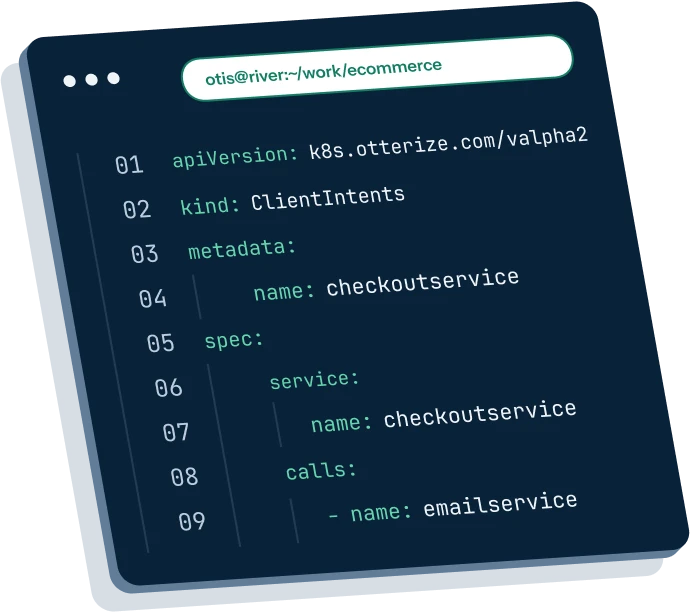
Client intents: your new best friend
Forget the hassle of managing pod identities and labels or diving deep into network policy configurations. Say hello to client intents—the easy way to set access controls.
Bootstrap with ease
Starting from scratch? No worries! Bootstrap client intents effortlessly by using network mapper to learn from existing traffic patterns.
- IBAC
Mastering Kubernetes networking: Otterize's journey in cloud-native packet management
Master Kubernetes networking with a comprehensive packet walk, and learn how Otterize helps build adaptive Network Policies.
- Zero-trust
Moving beyond perimeter security: Lessons from the TunnelVision attack
The recent "TunnelVision" attacks reinforce the need for a new security paradigm. Let's explore how this type of attack can be mitigated in the future and what tools we need.
- Network
Otter this world: How to chart Kubernetes egress traffic with Otterize
Discover how Otterize helps you gain visibility into your egress Kubernetes connections.